This Page is a Cheat Sheet for Linux. I have collected Info. from the internet and listed it here for easy access for me. If you find it useful then great!
” Everything in a file! ” Even your hardware! e.g. So when you play a movie it is moved into the Monitor file & Speaker file. Your just moving data from 1 file to another!. (This simple fact helped me understand how it all worked)
- All software must be installed as Admin – Sudo (super user do!)
- User accounts can use that software. A User can’t install software (That’s the security part of Linux) Viruses are software so if a user can’t install it …. Viruses can’t run!
- Daemons are the system software that runs in the background & is controlled by systemd.
The following illustration shows the architecture of a Linux system −
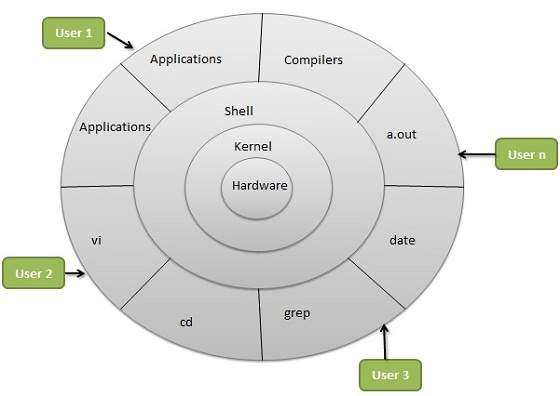
The architecture of a Linux System consists of the following layers −
Hardware layer − Hardware consists of all peripheral devices (RAM/ HDD/ CPU etc).
Kernel − It is the core component of Operating System, interacts directly with hardware, provides low level services to upper layer components.
Shell − An interface to kernel, hiding complexity of kernel’s functions from users. The shell takes commands from the user and executes kernel’s functions.
Utilities − Utility programs that provide the user most of the functionalities of an operating systems.
Linux Operating System has primarily three components
Kernel − Kernel is the core part of Linux. It is responsible for all major activities of this operating system. It consists of various modules and it interacts directly with the underlying hardware. Kernel provides the required abstraction to hide low level hardware details to system or application programs.
System Library − System libraries are special functions or programs using which application programs or system utilities accesses Kernel’s features. These libraries implement most of the functionalities of the operating system and do not requires kernel module’s code access rights.
System Utility − System Utility programs are responsible to do specialized, individual level tasks.
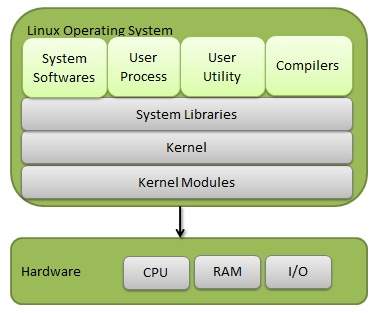
Kernel Mode vs User Mode
Kernel component code executes in a special privileged mode called kernel mode with full access to all resources of the computer. This code represents a single process, executes in single address space and do not require any context switch and hence is very efficient and fast. Kernel runs each processes and provides system services to processes, provides protected access to hardware to processes.
Support code which is not required to run in kernel mode is in System Library. User programs and other system programs works in User Mode which has no access to system hardware and kernel code. User programs/ utilities use System libraries to access Kernel functions to get system’s low level tasks.
Basic Features
Following are some of the important features of Linux Operating System.
Portable − Portability means software can works on different types of hardware in same way. Linux kernel and application programs supports their installation on any kind of hardware platform.
Open Source − Linux source code is freely available and it is community based development project. Multiple teams work in collaboration to enhance the capability of Linux operating system and it is continuously evolving.
Multi-User − Linux is a multiuser system means multiple users can access system resources like memory/ ram/ application programs at same time.
Multiprogramming − Linux is a multiprogramming system means multiple applications can run at same time.
Hierarchical File System − Linux provides a standard file structure in which system files/ user files are arranged.
Shell − Linux provides a special interpreter program which can be used to execute commands of the operating system. It can be used to do various types of operations, call application programs. etc.
Security − Linux provides user security using authentication features like password protection/ controlled access to specific files/ encryption of data.
Custom Kernels are also called micro-kernels, they are striping down versions of the full Kernel with everything you don’t need removed and only the hardware drivers needed.
A perfect example of this is the Raspberry Pi
Here is a guide for you. I always watch his videos,
Love this guys channel defensively bookmark it.
Another Kernel for Gamers & Streamers is XANMOD.
It’s a gaming Kernel, it fine for everyday workloads but with gaming & streaming is optimized.
Libraries are short scripts/programs that are used “in” other software. e.g.
Pick any program that has a menu. The menu (it has File, Edit, View, Options & Help.) Because Linux is open source, you can read the software! Most software would have the same code for there menu or very similar, so why code more than you need too. That’s where Libraries come in! Think LEGO for coders.
This makes coding faster on Linux. Less mistakes too and stops security issues from coming up. “OPEN SOURCE”
This “Libraries usage” extend into Drivers & Basic OS functions too. The Kernel is basically a collections of Libraries with priority assigned to them(Who gets processed first).
In Windows it’s “closed source” so each and every piece of software must be complete and you download the complete software on every update.
In Linux only the code that has to be updated/changed gets downloaded. As most of the program are Libraries only the main code that points to each library needs updating. This makes updating fast and small.
If you can think of 2 separate software on Linux that has the “same fetchers” odds are there is a Lib file or soon will be.
In Short Lib’s are “Common code that doesn’t change” that are used by many other programs.
This is why Linux is so small! (Linux iso size 2Gb(with all software) vs Windows 10 iso 8Gb!)
Linux filesystem structures and understand the meaning of individual high-level directories.
/ – Root
Every single file and directory starts from the root directory.
Only root user has write privilege under this directory.
Please note that /root is root user’s home directory, which is not same as /.
/bin – User Binaries
Contains binary executables.
Common linux commands you need to use in single-user modes are located under this directory.
Commands used by all the users of the system are located here.
For example: ps, ls, ping, grep, cp.
/sbin – System Binaries
Just like /bin, /sbin also contains binary executables.
But, the linux commands located under this directory are used typically by system aministrator, for system maintenance purpose.
For example: iptables, reboot, fdisk, ifconfig, swapon
/etc – Configuration Files
Contains configuration files required by all programs.
This also contains startup and shutdown shell scripts used to start/stop individual programs.
For example: /etc/resolv.conf, /etc/logrotate.conf
/dev – Device Files
Contains device files.
These include terminal devices, usb, or any device attached to the system.
For example: /dev/tty1, /dev/usbmon0
/proc – Process Information
Contains information about system process.
This is a pseudo filesystem contains information about running process. For example: /proc/{pid} directory contains information about the process with that particular pid.
This is a virtual filesystem with text information about system resources. For example: /proc/uptime
/var – Variable Files
var stands for variable files.
Content of the files that are expected to grow can be found under this directory.
This includes — system log files (/var/log); packages and database files (/var/lib); emails (/var/mail); print queues (/var/spool); lock files (/var/lock); temp files needed across reboots (/var/tmp);
/tmp – Temporary Files
Directory that contains temporary files created by system and users.
Files under this directory are deleted when system is rebooted.
/usr – User Programs
Contains binaries, libraries, documentation, and source-code for second level programs.
/usr/bin contains binary files for user programs. If you can’t find a user binary under /bin, look under /usr/bin. For example: at, awk, cc, less, scp
/usr/sbin contains binary files for system administrators. If you can’t find a system binary under /sbin, look under /usr/sbin. For example: atd, cron, sshd, useradd, userdel
/usr/lib contains libraries for /usr/bin and /usr/sbin
/usr/local contains users programs that you install from source. For example, when you install apache from source, it goes under /usr/local/apache2
/home – Home Directories
Home directories for all users to store their personal files.
For example: /home/john, /home/nikita
/boot – Boot Loader Files
Contains boot loader related files.
Kernel initrd, vmlinux, grub files are located under /boot
For example: initrd.img-2.6.32-24-generic, vmlinuz-2.6.32-24-generic
/lib – System Libraries
Contains library files that supports the binaries located under /bin and /sbin
Library filenames are either ld* or lib*.so.*
For example: ld-2.11.1.so, libncurses.so.5.7
/opt – Optional add-on Applications
opt stands for optional.
Contains add-on applications from individual vendors.
add-on applications should be installed under either /opt/ or /opt/ sub-directory.
/mnt – Mount Directory
Temporary mount directory where sysadmins can mount filesystems.
/media – Removable Media Devices
Temporary mount directory for removable devices.
For examples, /media/cdrom for CD-ROM; /media/floppy for floppy drives; /media/cdrecorder for CD writer
/srv – Service Data
srv stands for service.
Contains server specific services related data.
For example, /srv/cvs contains CVS related data.
The file system is the same for all Linux/Android systems, no matter how big or small they are! But How!?! Right!
A OS is not Installed on a Hard-drive, it is installed on a Partition. A Partition can be made up of several drives like in a RAID. Your BIOS of your computer points to a hard-drive that has a Bootable Partition = MBR or GPT. This then boots the OS Partition.
The hardware (hard-drives) & File structure are separate because of Partitions!
Think of C:/ on windows as Root (/). In Windows you can add a hard-drive as an extended partition(a folder on C:/) but if the original hard-drive dies then it’s dead too which is why it is generally given the D:/ and a shortcut is used.
But in Linux….
Linux is designed for expansion. Expansion while the machine is still running(Servers). Each folder can be moved to a new “Partition” while running & then the “daemon” can be reloaded for fstab (the file system software).
For example.
“ROOT” (/) & all software can be on a Very Fast but Small NVMe drives partition saving money and have “/Home”(Where your user data is stored) on a Huge slower spinning hard-drives partition or RAID’s partition!
https://help.ubuntu.com/community/Partitioning/Home/Moving
Remember Linux was made for Universities & Businesses where there are hundreds of users. Which is why there are 2 types : ADMIN vs USER.
This is also why your tweaks to programs are stored in your /Home folder too. Each user can tweak the same software but those “tweaks” only affect that user. Only a Admin account can make system wide changes like installing software.
If you want to really get into Linux, the only real way is to build it. Now there are 2 ways. Gentoo or Actually building Linux from scratch.
Which one should you do? First! Well that’s an easy one! Gentoo.
After if you really want to learn how everything, I mean everything works. Build your own!
I personally have not done this as I’m just a “User”! & I don’t care how it works just that it does! I Know I should but….. I don’t need to know how to bake a cake to be able to eat it! If you want deep knowledge of Linux these 2 are your best bet, and after your learning bug is satisfied you can join me on Kubuntu! LOL
Here is a video on KDE & it explains it all. KDE NEON might be a better fit for you!
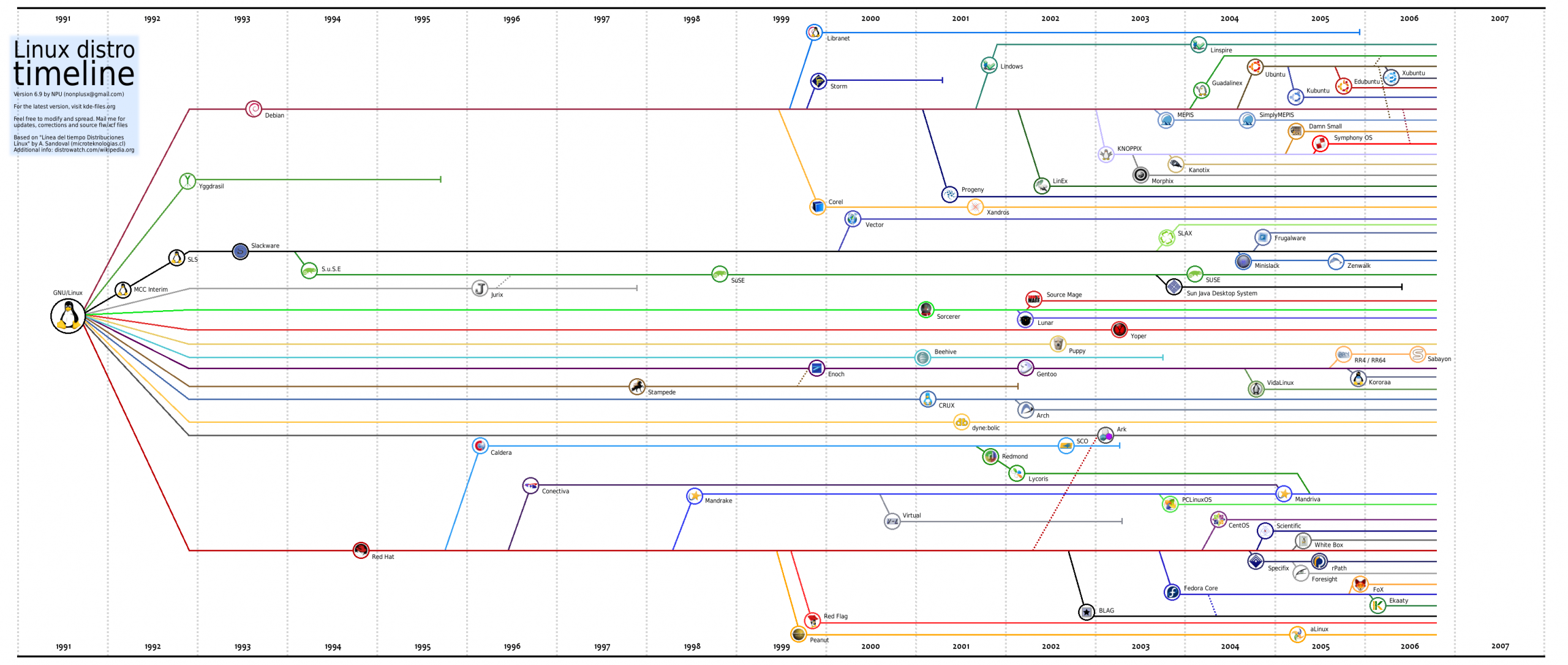
From the diagram you can see that there are many different distributions of Linux, in fact there are thousands and each one is unique. But that’s a longer story, and for another time!
The distro. that we are interested in is Debian.Why?
Debian is considered the grand father of Linux because it has been around from just about the beginning. It is a slow and stable distro. and so a lot of other distro.’s are based on it, like Ubuntu. (But the most important os is SteamOS. Steam has made Industry standards for game developers making Linux compatable for AAA games.)
Ubuntu is backed by a company called Canonical. There main focus is business software like servers and IOT devices. The desktop is a side business for them. So what’s different? PPA’s & SNAP’s…. How software is installed. We will get into installing software later.


User Interface (UI) or Desktop Enviroment (DE)
Unlike Apple or Microsoft that only have one desktop environment Linux has many, like – Gnome, KDE, LXqt, LXde, XFCE, i3, Mate, Cinnimon, budgie etc, etc. With each one being slightly different from the other.
Here is a site that has them all! “Distro Hopping” is a favorite past-time for every Linux user. Finding the right Linux for the job & hardware is always fun. The reason I have Guided you the Debian side is Help websites. Most will reference Ubuntu so it’s a great place to start! Have fun!
Distrowatch.com
Understanding Basic File Permissions and ownership in Linux
To view the permissions for files and directories, use the ls -l or ls –n commands.
# ls -l file -rw-r--r-- 1 root root 0 Nov 19 23:49 file
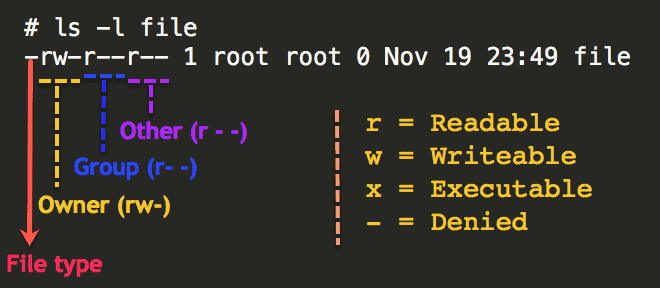
The first field of information displayed by the ls -l command is the file type. The file type typically specifies whether it is a file or a directory. A file is represented by a hyphen (-). A directory is represented by the letter d.
The remaining fields represent the permission groups: owner, group, and other.
There are three permissions groups:
- Owner
- Group
- Other
The table describes the permission groups and their scope:
| Permission | Description |
|---|---|
| Owner | Permissions used by the assigned owner of the file or directory |
| Group | Permissions used by members of the group that owns the file or directory |
| Other | Permissions used by all users other than the file owner, and members of the group that owns the file or the directory |
– Each permission group has three permissions, called a permission set.
– Each set consists of read, write, and execute permissions.
– Each file or directory has three permission sets for the three types of permission groups.
– The first permission set represents the owner permissions, the second set represents the group permissions, and the last set represents the other permissions.
– The read, write, and execute permissions are represented by the characters r, w, and x, respectively.
– The presence of any of these characters, such as r, indicates that the particular permission is granted.
– A dash (–) symbol in place of a character in a permission set indicates that a particular permission is denied.
– Linux assigns initial permissions automatically when a new file or directory is created.
| Permission | Access for a file | Access for a directory |
|---|---|---|
| Read (r) | You can display file contents and copy the file. | You can list the directory contents with the ls command. |
| Write (w) | You can modify the file contents. | You can modify the contents of a directory, such as by deleting a file. You must also have the execute permission for this to happen. |
| Execute (x) | You can execute the file if it is an executable. You can execute a shell script if you also have read and execute permissions. | You can use the cd command to access the directory. If you also have read access, you can run the ls -l command on the directory to list contents. If you do not have read access, you can run the ls command as long as you know the file name. |
Every file is owned by a specific user (or UID) and a specific group (or GID). The chown command can be used to change just the user, or the user and group of a file. Here is an example of changing the owner of file test to user and its group to user.
# ls -l test -rw-r--r-- 1 root root 0 Nov 20 00:43 test
# chown user:user test
# ls -l test -rw-r--r-- 1 user user 0 Nov 20 00:43 test
The basic format for the chown command is as follows:
# chown user:group filename
A period (.) can be used in place of the colon (:) separator character. Also, either the user or group name can be omitted. If the username is omitted (but the separator character is present), then the chown command behaves like the chgrp command, and only the group ownership is changed. If the group name is omitted (but the separator character is present, then the group will be set to the login group of the specified user. If both the group name and the separator character are omitted, then only the username is changed. For example, to change only the owner you could run the following:
# chown user filename
An alternate command to change only the group of a file is the chgrp command. For example:
# chgrp group filename
The chgrp command is commonly used by normal users to change the group ownership of their files. The chown command is normally used only by the root user.
Each user can be a member of many groups (listed in the /etc/group file under several groups). Only one group will be a user’s primary group (listed in the user’s entry in /etc/password). When a user creates a file, by default the file will be owned by the user’s primary group. If they want the file to be owned by one of their other groups, they must use the chgrp command to modify the group membership. For Example :
$ id uid=1001(user) gid=1001(user) groups=1001(user),10(wheel)
$ touch file
$ ls -lrt file -rw-rw-r-- 1 user user 0 Nov 20 00:52 file
As shown above the newly created file (file) automatically gets the group as “user”.
Below is sample output from ls -l command; you can see from the first character of each line that dir1 and dir2 are directories (indicated by the d) and that file1 and file2 are a regular file (indicated by the –).
$ ls -l total 0 drwxrwxr-x 2 user user 6 Nov 20 00:55 dir1 drwxrwxr-x 2 user user 6 Nov 20 00:55 dir2 -rw-rw-r-- 1 user user 0 Nov 20 00:55 file1 -rw-rw-r-- 1 user user 0 Nov 20 00:55 file2
The next nine characters show the file’s permissions for user, group, and others (or everyone else) as shown below, with parentheses added for clarity:
-(rw-)(rw-)(r--) 1 user user 0 Nov 20 00:55 file1
Now the owner has read and write permissions (rw-), the group has read and write permissions (rw-), and everyone else has only read permissions (r–). This is called symbolic representation because letters such as r, w, and x, are used to indicate permissions.
Permissions can also be represented numerically:
r = 4; w = 2; x = 1
Add each section so that the permissions of the file meta (from the example above) would be 664. Here is another way to look at how we come to that number:
-(rw-)(rw-)(r--) -(42-)(42-)(4--) 664
Adding the numbers in each section results in permissions of 664.
File permission can be represented in a numeric or symbolic format.The permission number can consist of three or four digits, ranging from 0 to 7.
When 3 digits number is used, the first digit represents the permissions of the file’s owner, the second one the file’s group and the last one all other users.
The write, read, and execute permissions have the following number value:
r(read) = 4w(write) = 2x(execute) = 1- no permissions = 0
The permissions digit of a specific user class is the sum of the values of the permissions for that class.
Each digit of the permissions number may be a sum of 4, 2, 1 and 0:
- 0 (0+0+0) – No permission.
- 1 (0+0+1) – Only execute permission.
- 2 (0+2+0) – Only write permission.
- 3 (0+2+1) – Write and execute permissions.
- 4 (4+0+0) – Only read permission.
- 5 (4+0+1) – Read and execute permission.
- 6 (4+2+0) – Read and write permissions.
- 7 (4+2+1) – Read, write, and execute permission.
For example, if the permission number is set to 750 it means that the file’s owner has read, write and execute permission, file’s group has read and execute permissions, and other users have no permissions:
- Owner: rwx=4+2+1=7
- Group: r-x=4+0+1=5
- Others: r-x=0+0+0=0
When the 4 digits number is used, the first digit has the following meaning:
- setuid=4
- setgid=2
- sticky=1
- no changes = 0
The next three digits have the same meaning as when using 3 digits number. If the first digit is 0 it can be omitted, and the mode can be represented with 3 digits. The numeric mode 0755 is the same as 755.
To view the file’s permissions in the numeric (octal) notation, use the stat command:
stat -c "%a" filename
644
Setting 777 permissions to a file or directory means that it will be readable, writable and executable by all users and may pose a huge security risk.
For example, if you recursively change the permissions of all files and subdirectories under the /var/www directory to 777, any user on the system will be able to create, delete or modify files in that directory.
If you experience permission issues with your web server, instead of recursively setting the permission to 777, change the file’s ownership to the user running the application and set the file’s permissions to 644 and directory’s permissions to 755.
File ownership can be changed using the chown command and permissions with the chmod command.
Let’s say you have a PHP application on your server running as user “linuxize”. To set the correct permissions you would run:
chown -R linuxize: /var/wwwfind /var/www -type d -exec chmod 755 {} \;find /var/www -type f -exec chmod 644 {} \;
Only root, the file owner, or user with sudo privileges can change the permissions of a file. Be extra careful when using chmod, especially when recursively changing the permissions
The chmod command is used to alter the permissions of a file. It may be used to add or remove permissions symbolically. For example, to add execute permissions for the owner of a file you would run:
$ chmod u+x file_name
Or, to add read and write permissions for the group that owns the file, you would run:
$ chmod g+rw file_name
Instead of adding permissions, the symbolic syntax of chmod can also be used to subtract or set to some absolute value as shown in these examples:
$ chmod o-w file_name $ chmod u=rwx,g=rx,o= file_name
The chmod command can also explicitly set permissions using a numerical representation. For example, to set permissions on a file to rwxrwxr–, you would run:
$ chmod 774 file_name
In addition to the standard read, write, and execute permissions, chmod can also set special permissions. These are the setuid bit, the setgid bit, and the sticky bit. The following examples show setting each of these special permissions along with brief descriptions of the effect of those permissions.
$ chmod u+s file_name
Adds the setuid bit so that, if executable, this file will execute with the permissions of its owner.
$ chmod g+s file_name
Adds the setgid bit so that, if executable, this file will execute with the permissions of its group. When this is set on a directory, all files created in the directory will have the same group as the directory.
$ chmod o+t directory_name
Adds the sticky bit so that users can only delete files from this directory that they created.
- https://linuxize.com/post/what-does-chmod-777-mean/
- https://www.thegeekdiary.com/understanding-basic-file-permissions-and-ownership-in-linux/
- https://www.thegeekstuff.com/2010/09/linux-file-system-structure/
- https://www.tutorialspoint.com/operating_system/os_linux.htm
You should understand “system software”,”user software”, Who has permissions to all files for reading, writing & execution. & How to install software for users.
There is you the owner “User”, group for your files is normally you too.
But there are system files so group “Sudo” needs access to execute a system program. & groups for each part of the OS , sound, USB, graphics etc etc …. All with permissions creating more security!